Problem
We have three FreeIPA administrative panel hosts (freeipa01.inside.mydomain.ru, freeipa02.inside.mydomain.ru and freeipa03.inside.mydomain.ru). We needed to provide access to them by one domain name: freeipa.mydomain.ru. Despite the seeming simplicity of the task, we had to work hard to solve it, because there were no ready-made recipes for HAProxy version 2.0 and higher on the internet.
Each FreeIPA installation is bound to a different domain name, which means that we will need to edit the headers of incoming and outgoing HTTP requests. The self-service portal must be closed with a valid certificate, and the FreeIPA hosts running on the backend must not be modified so as not to affect client-server communication through the API.
Solution
First, we need to edit the default HAProxy configuration file. There are four sections: global, defaults, frontend and backend. We won't touch the first two (the standard values are enough), but we will describe frontend and backend in detail:
#frontend section
frontend main
bind :80
redirect scheme https code 301 if !{ ssl_fc } # redirect to https frontend main_ssl
bind :443 ssl crt /etc/haproxy/ssl/ # use certificates from the directory
use_backend freeipa if { ssl_fc_sni freeipa.mydomain.ru } # if freeipa.mydomain.ru is accessed, use FreeIPA backend
#backend section
backend freeipa
mode http
balance roundrobin # distribute the load across the hosts one by one
cookie SERVERID insert indirect nocache httponly secure # add a cookie to direct traffic based on it
#acl for request based on added cookie
acl hdr_req_ipa01 req.hdr(Cookie) -m sub ipa01
acl hdr_req_ipa02 req.hdr(Cookie) -m sub ipa02
acl hdr_req_ipa03 req.hdr(Cookie) -m sub ipa03
#--------------------------------------------------------------------------
#Depending on which cookie our request is labeled with, we change the Host and Referer headers
http-request set-header Host freeipa01.inside.mydomain.ru if hdr_req_ipa01
http-request replace-header Referer ^https?://freeipa\.mydomain\.ru(.*)$ https://freeipa01\.inside\.mydomain\.ru\1 if hdr_req_ipa01
http-request set-header Host freeipa02.inside.mydomain.ru if hdr_req_ipa02
http-request replace-header Referer ^https?://freeipa\.mydomain\.ru(.*)$ https://freeipa01\.inside\.mydomain\.ru\1 if hdr_req_ipa02
http-request set-header Host freeipa03.inside.mydomain.ru if hdr_req_ipa03
http-request replace-header Referer ^https?://freeipa\.mydomain\.ru(.*)$ https://freeipa01\.inside\.mydomain\.ru\1 if hdr_req_ipa03
#--------------------------------------------------------------------------
#acl for response based on Location header
acl hdr_ipa01 res.hdr(Location) -m sub freeipa01.inside.mydomain.ru
acl hdr_ipa02 res.hdr(Location) -m sub freeipa02.inside.mydomain.ru
acl hdr_ipa03 res.hdr(Location) -m sub freeipa03.inside.mydomain.ru
#--------------------------------------------------------------------------
#Depending on which host the response comes from, we edit the Set-Cookie and Location headers. If we do not edit the Location header we will encounter the following problem: when a user clicks on the freeipa.mydomain.ru link he will be redirected to one of the hosts: freeipa0x.inside.mydomain.ru (this is an important point, omitted in all the manuals we consulted).
http-response replace-header Set-Cookie ^Domain=freeipa01\.inside\.mydomain\.ru(.*) Domain=freeipa\.mydomain\.ru\1 if hdr_ipa01
http-response replace-value Location ^https?://freeipa01\.inside\.mydomain\.ru(.*)$ https://freeipa\.mydomain\.ru\1 if hdr_ipa01
http-response replace-header Set-Cookie ^Domain=freeipa02\.inside\.mydomain\.ru(.*) Domain=freeipa\.mydomain\.ru\1 if hdr_ipa02
http-response replace-value Location ^https?://freeipa02\.inside\.mydomain\.ru(.*)$ https://freeipa\.mydomain\.ru\1 if hdr_ipa02
http-response replace-header Set-Cookie ^Domain=freeipa03\.inside\.mydomain\.ru(.*) Domain=freeipa\.mydomain\.ru\1 if hdr_ipa03
http-response replace-value Location ^https?://freeipa03\.inside\.mydomain\.ru(.*)$ https://freeipa\.mydomain\.ru\1 if hdr_ipa03
#--------------------------------------------------------------------------
#Here we put our FreeIPA hosts
server ipa01 freeipa01.inside.mydomain.ru:443 check port 443 inter 5s rise 2 fall 5 cookie ipa01 weight 9 ssl verify none
server ipa02 freeipa02.inside.mydomain.ru:443 check port 443 inter 5s rise 2 fall 5 cookie ipa02 weight 1 ssl verify none
server ipa03 freeipa03.inside.mydomain.ru:443 check port 443 inter 5s rise 2 fall 5 cookie ipa03 weight 3 ssl verify none
#check port 443 - check if the host is alive on port 443.
#inter 5s - check availability at 5 second intervals.
#rise 2 fall 5 - if 2 checks say that the host is unavailable, it will be excluded from balancing and returned after 5 successful checks.
#cookie ipa0x - specifies which cookie will be added as the SERVERID insert cookie.
#ssl verify none - SSL certificate termination, ignoring errors.
#weight 3 - specifies load balancing priority.There is also the possibility of encountering an annoying authorization window in Chrome, Edge, IE and some other browsers.
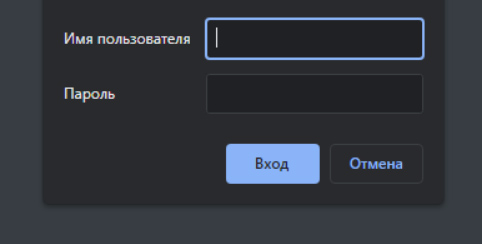
The appearance of this window is described in this bug report, which contains a solution to the problem, but with HAProxy you can solve the problem without changing the host configuration. To do that, we add the following line to the backend section of the configuration file:
http-response del-header www-authenticateIt will remove the header responsible for the intrusive window.
Conclusion
HOSTKEY always supports the initiative of its employees, which has a positive effect on the customer experience and development of the company. Not only do we help our specialists to develop and make a career (which again is beneficial for us as the employer), but we also get useful solutions for our customers, as well as interesting entries for the company blog. We hope that this solution will come in handy for our readers.