SSH key generation¶
In this article
Using SSH keys allows you to avoid entering the remote user's password and replace it with a hard-to-find SSH key, making the process of server management more secure.
Information
An SSH key is a cryptographic key used to authenticate a user when connecting to a remote server using the SSH protocol.
There are two types of SSH key:
-
A public key is key that can be sent to a remote server for identification. It is used to encrypt data that can only be decrypted with the corresponding private key. The private key can also be used to encrypt data, which is then decrypted by the public key.
-
A private key is a key that must be kept secret on the user's local machine. It is used to decrypt data encrypted with the public key.
To connect to a server using SSH keys, you need to create a key pair (public and private) on the local machine and then copy the public key to the remote server. It is then possible to connect to the server without providing the remote user's password. Usually the private key is generated with a password, and you will still need to provide that password when connecting.
SSH key generation for Linux/MacOS operating systems¶
Create an SSH key¶
-
Connect to the server via SSH.
-
Generate an SSH key on the local machine. To do this, run the following command in a terminal:
After running the command, you will be asked to select a filename and location for the key. By default it is stored in the
/.ssh/directory and the file name isid_rsa.You will then be prompted to enter a passphrase to further secure the SSH connection. You do not have to enter the passphrase:
Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again:The fingerprint of the key and its image appear on the terminal:
The key's randomart image is: +---[RSA 3072]----+ | . ..o+=| | . . o +.| | o . o . o.o| | = o . + oo| | . S . + o o| | . = ..o . | | o ..=o+ | | ..+=Xo+ | | .E=*=Oo | +----[SHA256]-----+You can use commands to view the SSH keys created:
cat ~/.ssh/id_rsa- private key lookup;cat ~/.ssh/id_rsa.pub- public key lookup.
Next you need to add the public key to the server. To do this, type the following command, replacing
usernamewith the username on the server andip_addresswith the IP address of the server:- <username> — username;
- <ip_address> — server public IP address.
After entering the command, the system will prompt for the password of the account on the server. After entering the password, the public key is copied to the server and added to the
~/.ssh/authorised_keysfile on the server.Once you have completed the above steps, you will need to enter the command to connect to the server using an SSH key:
Creating an SSH key during an Linux reinstall¶
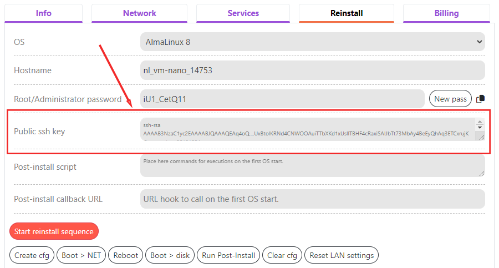
The SSH key can be added during the reinstallation of the operating system. To do this, before starting the installation of a new operating system in Invapi, fill in the Public ssh key field in the Reinstall tab:
Note
For an example of an OS reinstallation request, see OS reinstallation API methods
SSH key generation for Windows¶
Information
There are two methods of generating SSH keys on the Windows operating system: one using the OpenSSH client and one using the PuTTY client. Below are instructions for generating keys using either method.
OpenSSH client¶
To generate an SSH key using the OpenSSH client, you need to perform the following sequence of actions:
-
Check for the presence of the OpenSSH client. To do this, go to Parameters >> Applications >> Additional Components and type
SSHin the search bar: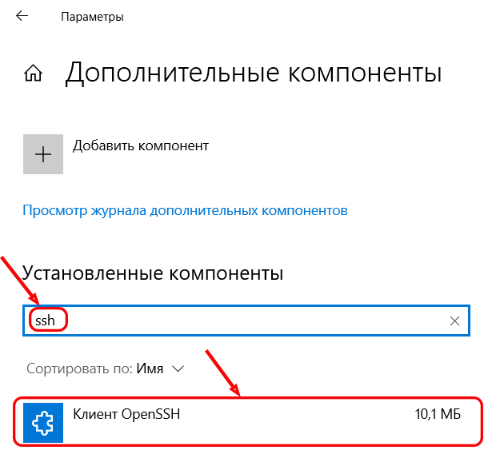
If the client is not installed, click the
Add Componentbutton and locate it using the search bar. Then click theInstallbutton.You can also use the command line to check for the openSSH client:
-
Go to the command prompt (shortcut Win+R >> type
cmd>> pressOK) and enter the command:After running the command, you will be asked to select a filename and location for the key. By default, it is stored in the
/.ssh/directory and the file name isid_rsa.You will then be prompted to enter a passphrase to further secure the SSH connection. This is optional:
Enter file in which to save the key (.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again:```The fingerprint of the key and its image appear on the terminal:
-
To check for generated keys, change to the previously specified directory on the local device. For example,
C:\Users\user_name\.ssh: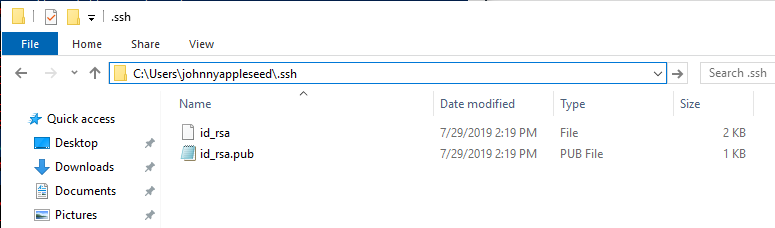
PuTTY¶
-
Download and install the Putty client on your local device;
-
Run
puttygen.exefrom theStartmenu. -
Select the
RSAkey type and press theGeneratebutton: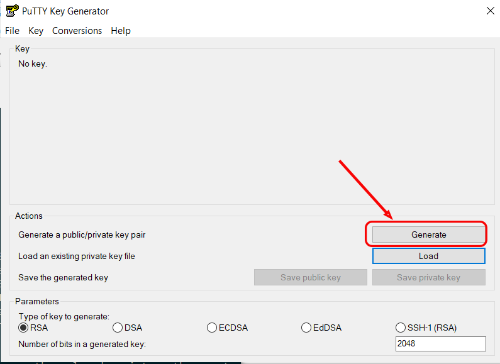
-
Move the mouse several times in random directions in the Key Generation window, this action will create a random noise:
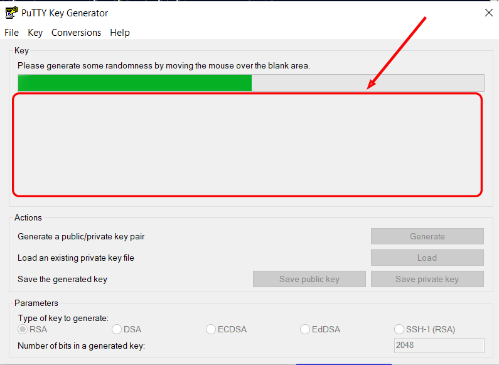
-
To protect the key with a password, enter it in Key passphrase and repeat it in Confirm passphrase. If no additional protection is required, leave these fields blank:
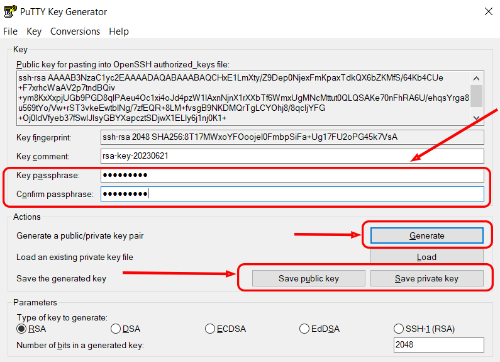
Click the Save Private Key button to save the private key.
Click the Save Public Key button to save the public key to disk. This key will be used for authentication on the server.
-
Copy the SSH public key to the server:
- </path/to/file> — full path to the public key on the local computer;
- <username> — username;
- <ip_address> — server public IP address;
- </path/to/destination> — path for storing the public key on the server.
Creating an SSH key during an Windows reinstall¶
It is possible to add the SSH key during the reinstallation of the operating system. To do this, before starting the installation of a new operating system in Invapi, fill in the Public ssh key field in the Reinstall tab:
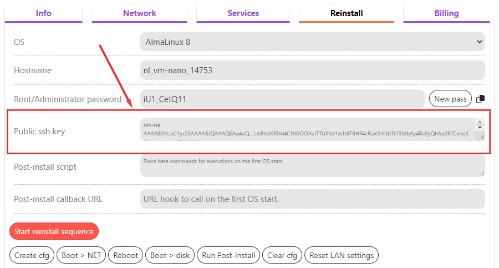
Note
For an example of an OS reinstallation request, see OS reinstallation API methods
Delete SSH key¶
To delete an SSH key, you must
- Open the
authorised_keysfile, which is usually located in the/.ssh/directory. You can use a command line text editor such as Vim or Nano. - Locate the line containing the public key you wish to delete. Each line corresponds to a key.
- Delete the line with the public key you want to remove from the
authorized_keysfile. - Save the changes and close the file.
- Restart the SSH service on the server for the changes to take effect. In most cases this can be done with
sudo service ssh restartorsudo systemctl restart sshd. - Check that the key no longer works for SSH login.
Note
If the WIndows OS is installed on the user's local device, you can also find the known_hosts file and delete the line with the appropriate SSH key in it.